Ransomware is one of the greatest emerging cybercrime challenges. Ransomware is the largest malware taxonomy and most phishing emails in 2016 contain ransomware. The tactic of ransomware is to hold the victim to extortion by encrypting the victim’s documents, files or disks until the person pays a ransom fee via bitcoin or voucher.
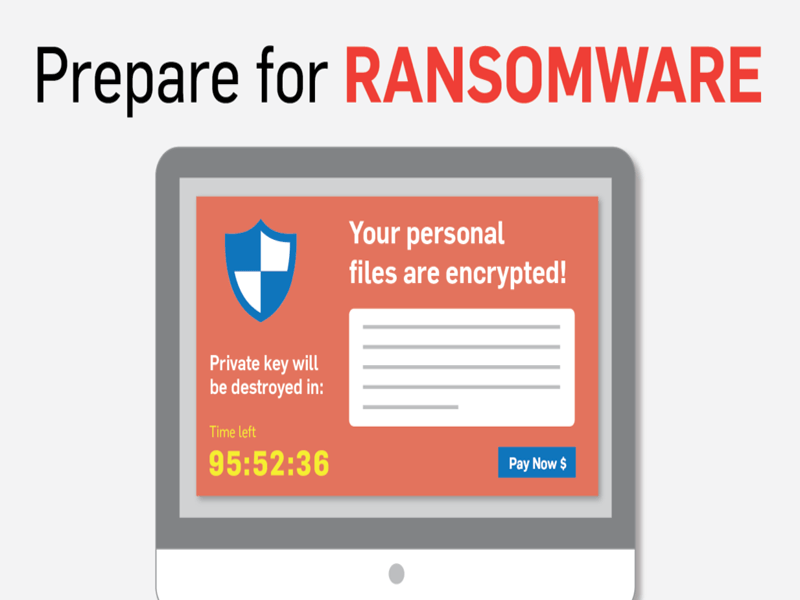
A ransomware infection comes in great number of forms. Ransomware targets all types of sensitive data that leads to a successful extortion. Extortion is often in the kind of where files are encrypted until the user pays for the key – such as cryptolocker malware that was prevalent in a few years ago. Cryptolocker malware encrypts files on the victim’s drive. The private key is contained on the criminal’s botnet server. The victim must pay the criminal to obtain the key to recover their files or access to the drive.
The growth in ransomware has occurred just in the past few years. It is getting easier to send ransomware and it offers a quick and easy return on investment. As the cost of deploying and controlling ransomware becomes lower, the extortion fee can also be reduced. The criminal maintains the margin whilst it becomes easier and more likely for the victim to just pay the fee.
Victims of ransomware phishing emails are generally soft targets. The audience has become a little more skeptical to the traditional finance / banking types of emails. But as ransomware emails are more recent phenomena the user can easily be duped into clicking on the link or attachment.
These newer phishing emails can often be targeted similar to a spear phishing campaign with personal details or a more general social engineering component, such a “thank you for your Resume”.

